Session Hijacking Explained Session is another very useful object that will hold any information For instance when user logged in to the system you want to hold his authorization level GetUserAuthorizationLevel some
session term semester session the part of a year during which a school or university has classes term E seleniummon exceptions SessionNotCreatedException Message session not created probably user data directory is already in use please specify a unique value for
Session Hijacking Explained
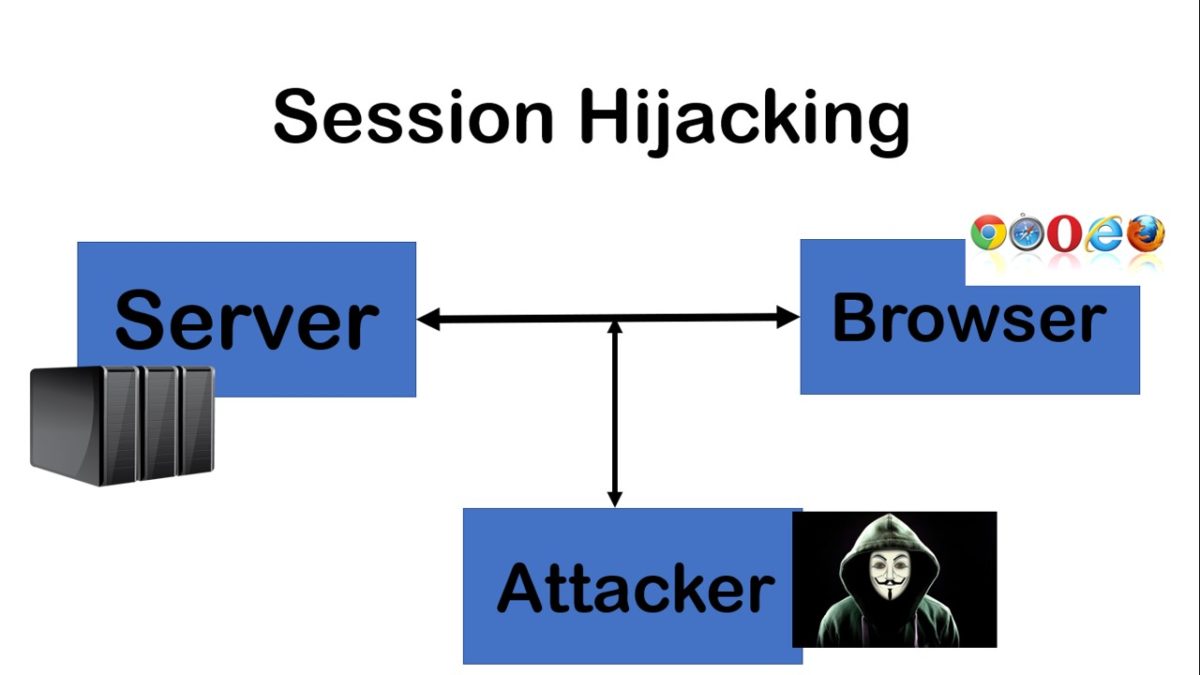
Session Hijacking Explained
https://allabouttesting.org/wp-content/uploads/2018/04/Session-Hijacking-cover-1200x675.jpg
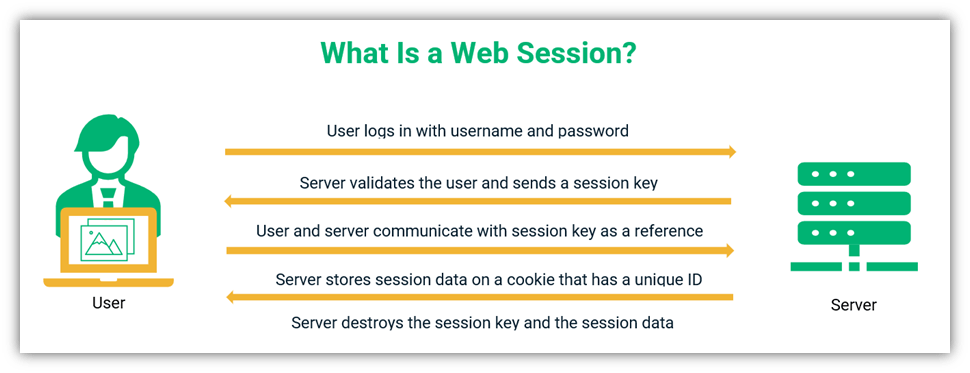
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/what-is-a-session.png
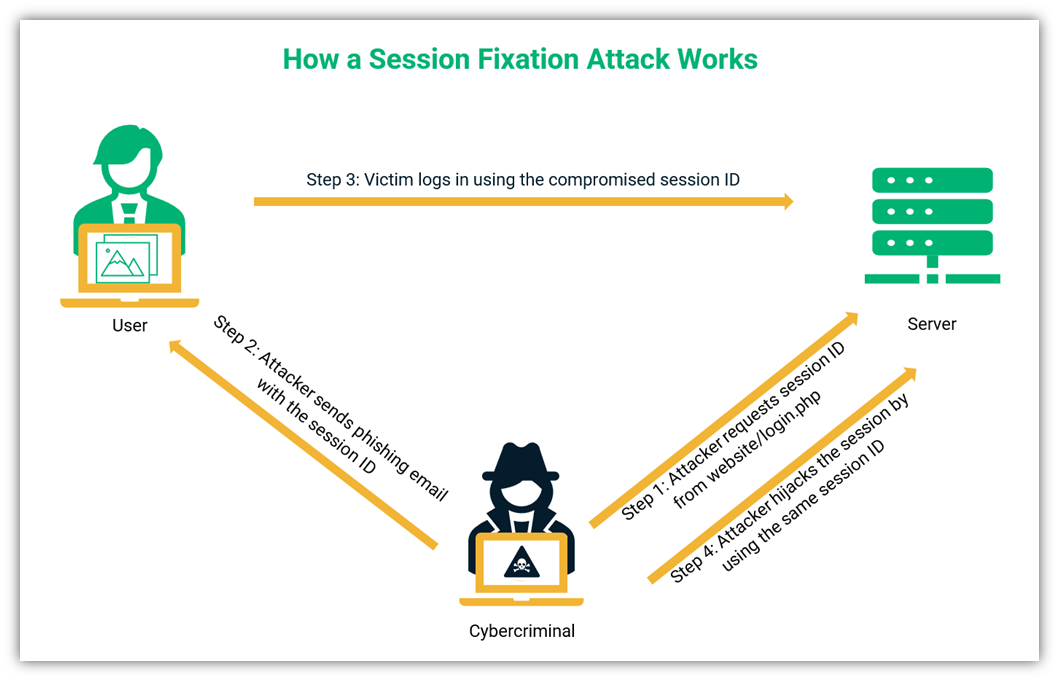
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/how-session-fixation-works.png
Because default session is limited to the profile or instance profile used sometimes you need to use the custom session to override the default session configuration e g Session Storage It is same like local storage date except it will delete all windows when browser windows closed by a web user In Session storage can store upto 5 mb data
Terminates a session LOGOFF sessionname sessionid SERVER servername V VM sessionname The name of the session sessionid The ID of the session While launching the Chrome driver I am getting Session not created from timeout 1 chrome opens for a second and crashes using selenium 3 mac OS 10 13 5 chrome 70
More picture related to Session Hijacking Explained
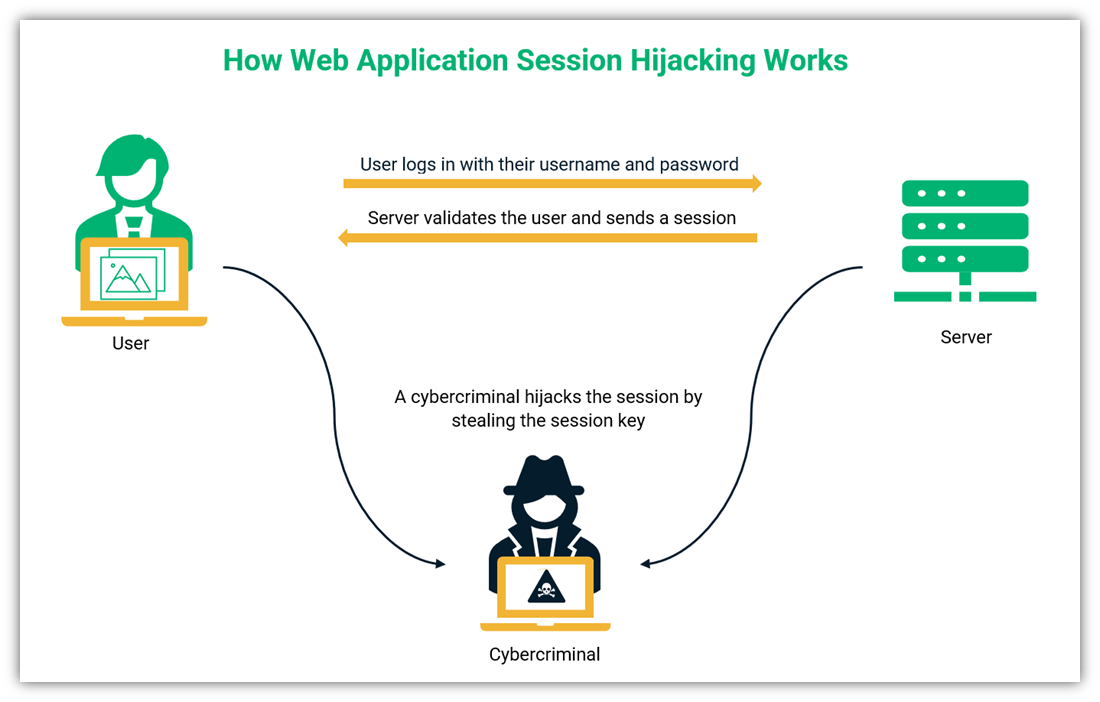
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/how-session-hijacking-works.png

A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/session-hijacking-fun-illustration-1024x737.png
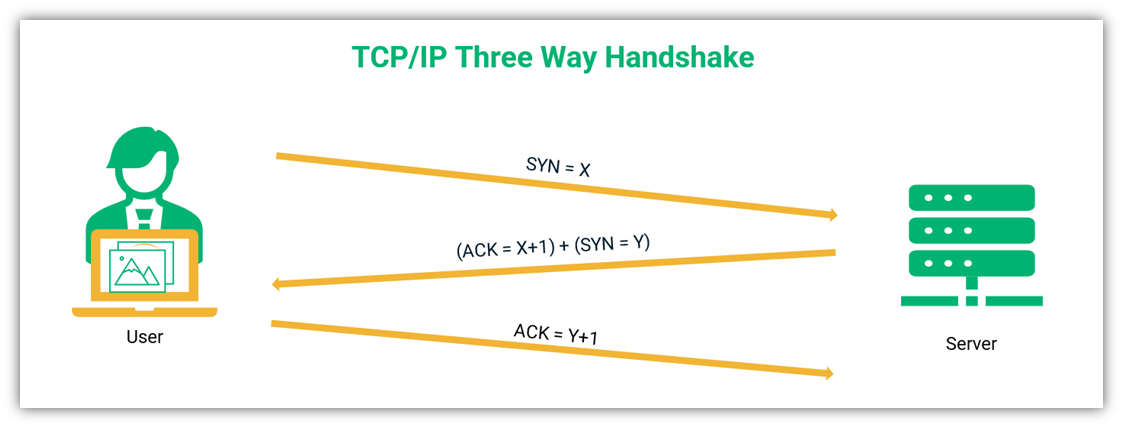
A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/tcp-ip-3-way-handshake.png
You can kill a detached session which is not responding within the screen session by doing the following Type screen list to identify the detached screen session screen ERROR database database name is being accessed by other users DETAIL There are 1 other session s using the database I ve tried shutting down the processes I see from a ps ef grep
[desc-10] [desc-11]

A Look At Session Hijacking Attacks Session Hijacking Explained
https://sectigostore.com/blog/wp-content/uploads/2021/10/session-hijacking-feature.jpg

The WKCR Hijacking Explained YouTube
https://i.ytimg.com/vi/0sAFXCti0vA/maxresdefault.jpg

https://stackoverflow.com › questions
Session is another very useful object that will hold any information For instance when user logged in to the system you want to hold his authorization level GetUserAuthorizationLevel some

https://zhidao.baidu.com › question
session term semester session the part of a year during which a school or university has classes term

Session Hijacking Explained YouTube

A Look At Session Hijacking Attacks Session Hijacking Explained

Session Hijacking Explained In Cyber Security YouTube

Session Hijacking Explained shorts YouTube

The Ultimate Threat DDoS DoS Sniffers And Session Hijacking Explained

What Are Session Tokens In Web Applications Session Hijacking

What Are Session Tokens In Web Applications Session Hijacking

How Do Hackers Beat Multifactor Authentication Session Hijacking

Credential Abuse Session Hijacking Video Step By Step In Hindi

Identipedia Authentication And Identity Concepts Explained
Session Hijacking Explained - [desc-12]