What Is The Role Of Information Security Policy 2018 04 16 1 character 2 role
role character role 1 character Play a role in 1 ple r l n ple ro l n 2 3 role in of for role
What Is The Role Of Information Security Policy

What Is The Role Of Information Security Policy
https://helpfulprofessor.com/wp-content/uploads/2022/12/group-roles-for-students.jpg

Youth And SDGs United Nations Development Programme
https://www.undp.org/sites/g/files/zskgke326/files/migration/np/UNDP_NP-youth-and-sdgs-Nepali.jpg
https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https://substack-post-media.s3.amazonaws.com/public/images/da463826-28d6-492b-a94e-a9c13ecbba72_1772x1288.png
Play a role in doing play a role in ple r l n ple ro l n v acting on kt n kt n role r l ro l n 1 He was invited to play a role in this TV play 2 We will get commercial insurance to play a role in improving the social securitysystem
CRPG Computer Role Playing Game COI Declaration of Interest forms from all the authors of an article is required for every submiss
More picture related to What Is The Role Of Information Security Policy

Role Based Access Control RBAC CyberHoot
https://cyberhoot.com/wp-content/uploads/2021/02/5c195c704e91290a125e8c82_5b172236e17ccd3862bcf6b1_IAM20_RBAC.jpeg
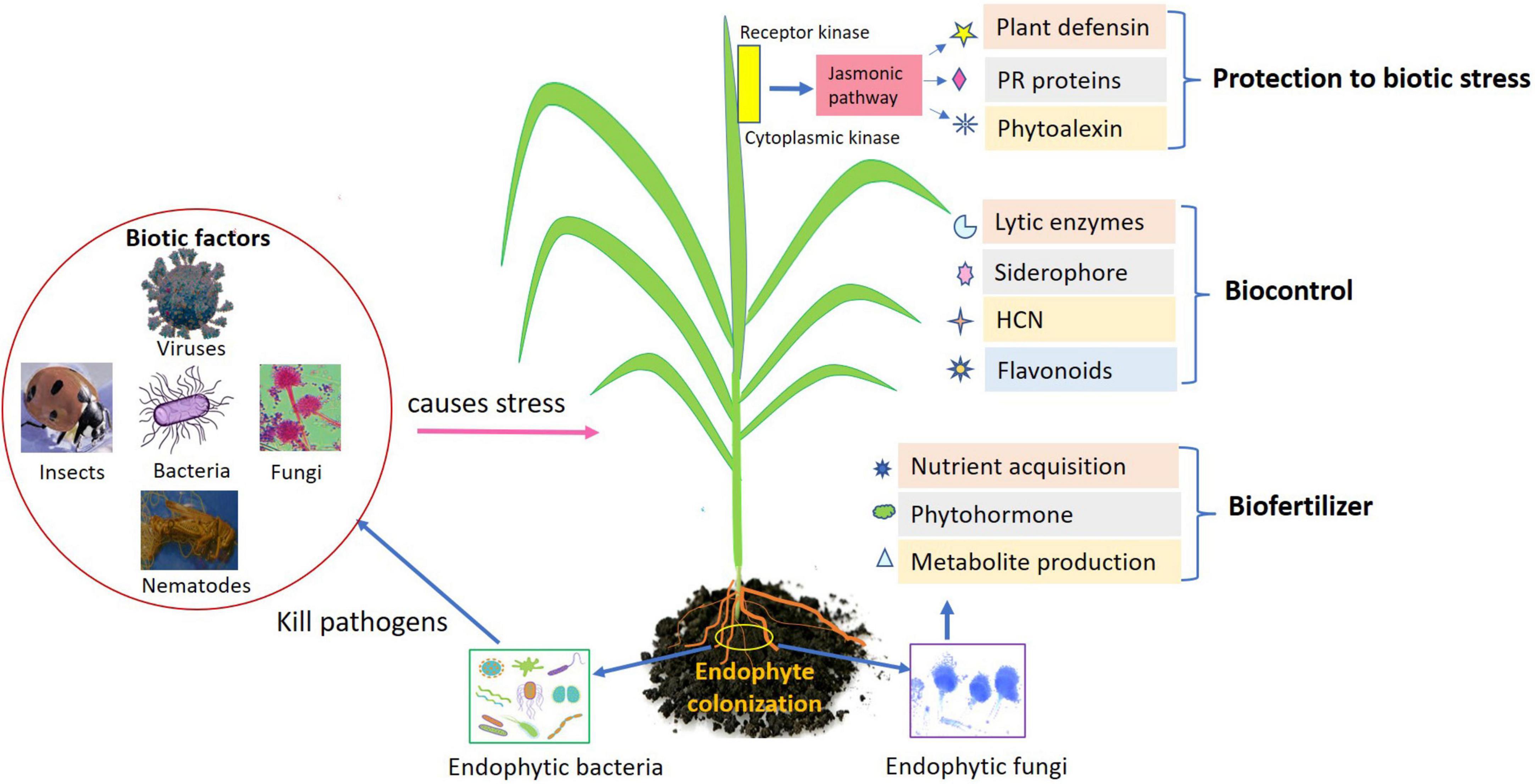
Jaz Bael
https://www.frontiersin.org/files/Articles/933017/fmicb-13-933017-HTML-r1/image_m/fmicb-13-933017-g001.jpg

Cyber Security Awareness Poster 10924170 Vector Art At Vecteezy
https://static.vecteezy.com/system/resources/previews/010/924/170/original/cyber-security-awareness-poster-free-vector.jpg
job The corresponding author is responsible for ensuring that the descriptions are accurate and agreed by all authors The role s of all authors should be listed using the relevant above
[desc-10] [desc-11]
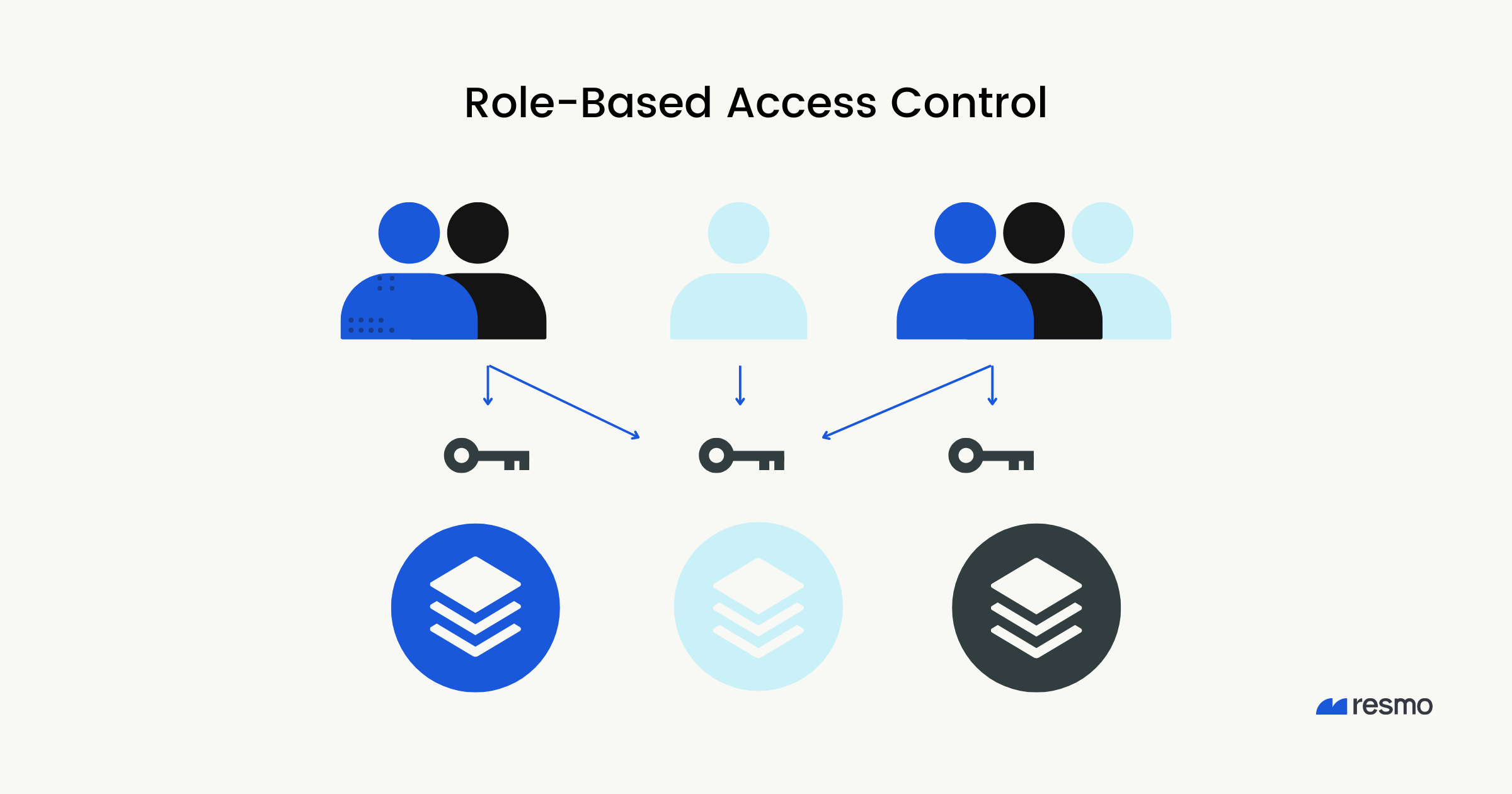
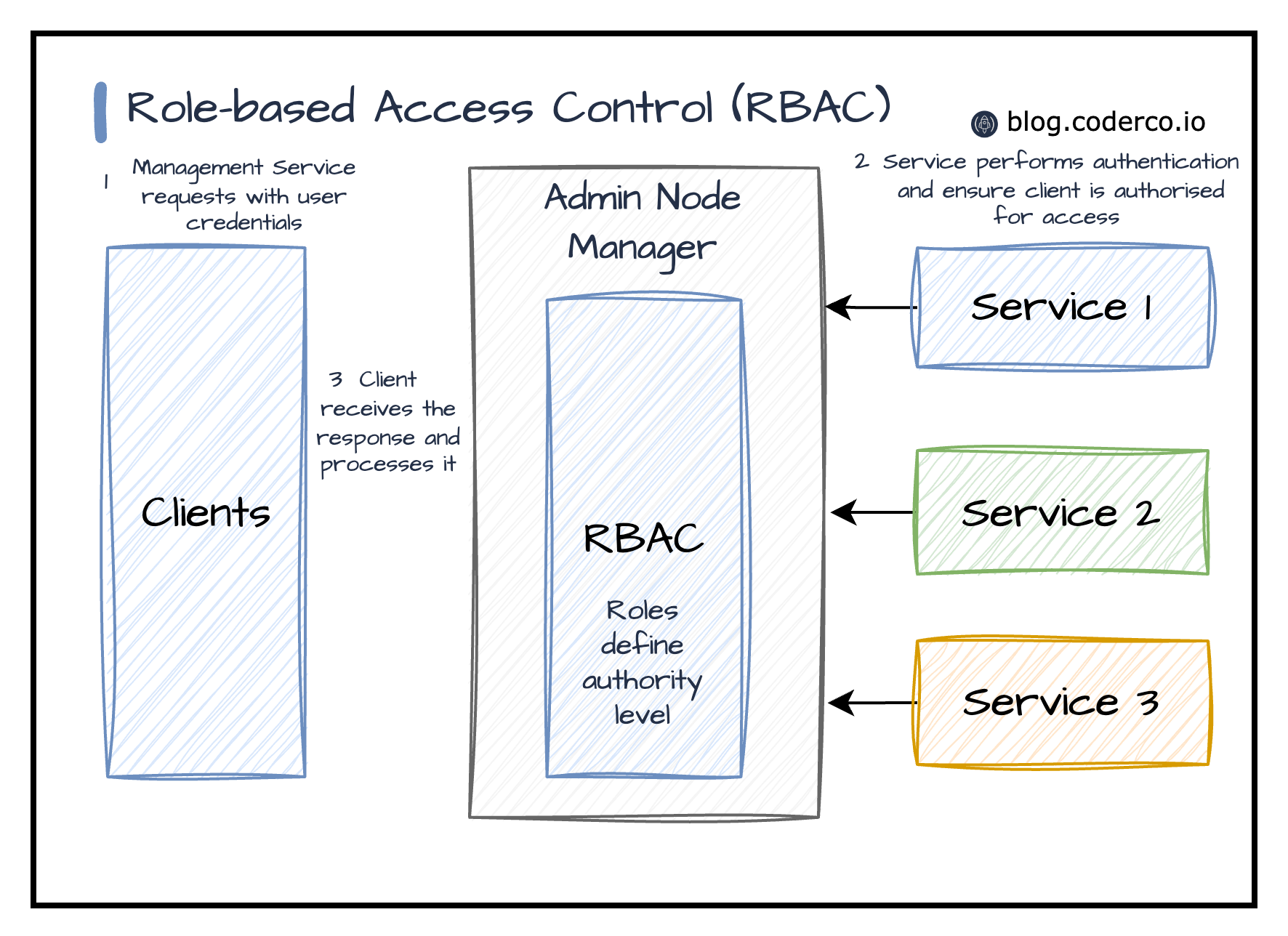
Introducing Role Based Access Control RBAC Management Resmo
https://uploads-ssl.webflow.com/5f5097f276b52f2a32f9c27a/63bacae528e10747f296f56a_role-based-access-control.png

What Is The Role Of The Syndicate
https://www.debtbook.com/hubfs/Learning Center - Debt.png


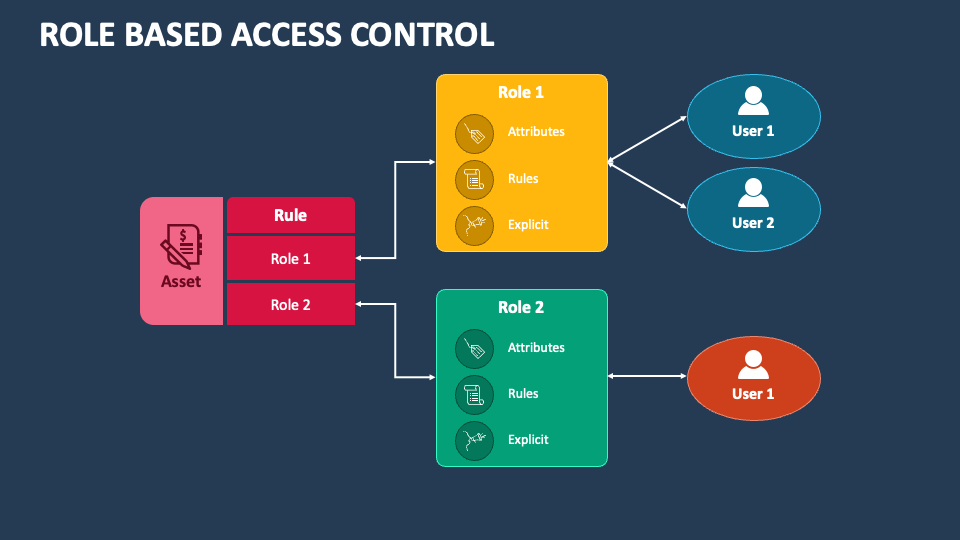
Izvinjenje Hodnik Regan Role Based Access Control Zvu nik Vrijednost Crta

Introducing Role Based Access Control RBAC Management Resmo

Reconciliation As The Final Stage Of Conflict Resolution Lid M sta

Information Security Roles Responsibilities Team Organizational

Auditor Responsibilities Types Guidelines Skills Required

Brace Yourself Cybersecurity Threats Are On The Rise

Brace Yourself Cybersecurity Threats Are On The Rise

ERP In Supply Chain Management A Detailed Guide

Family Roles

Security Awareness Policy Template
What Is The Role Of Information Security Policy - 1 He was invited to play a role in this TV play 2 We will get commercial insurance to play a role in improving the social securitysystem